TryHackMe - Neighbour Walkthrough
Room: Neighbour
Author: cmnatic
Difficulty: Easy
In this challenge we will be exploiting IDOR or the Insecure Direct Object Reference vulnerability. IDOR allows the attacker to bypass authorization mechanisms to access information/resources directly by manipulating the value of a parameter used to point to that resource/object.
Information Gathering / Initial Access
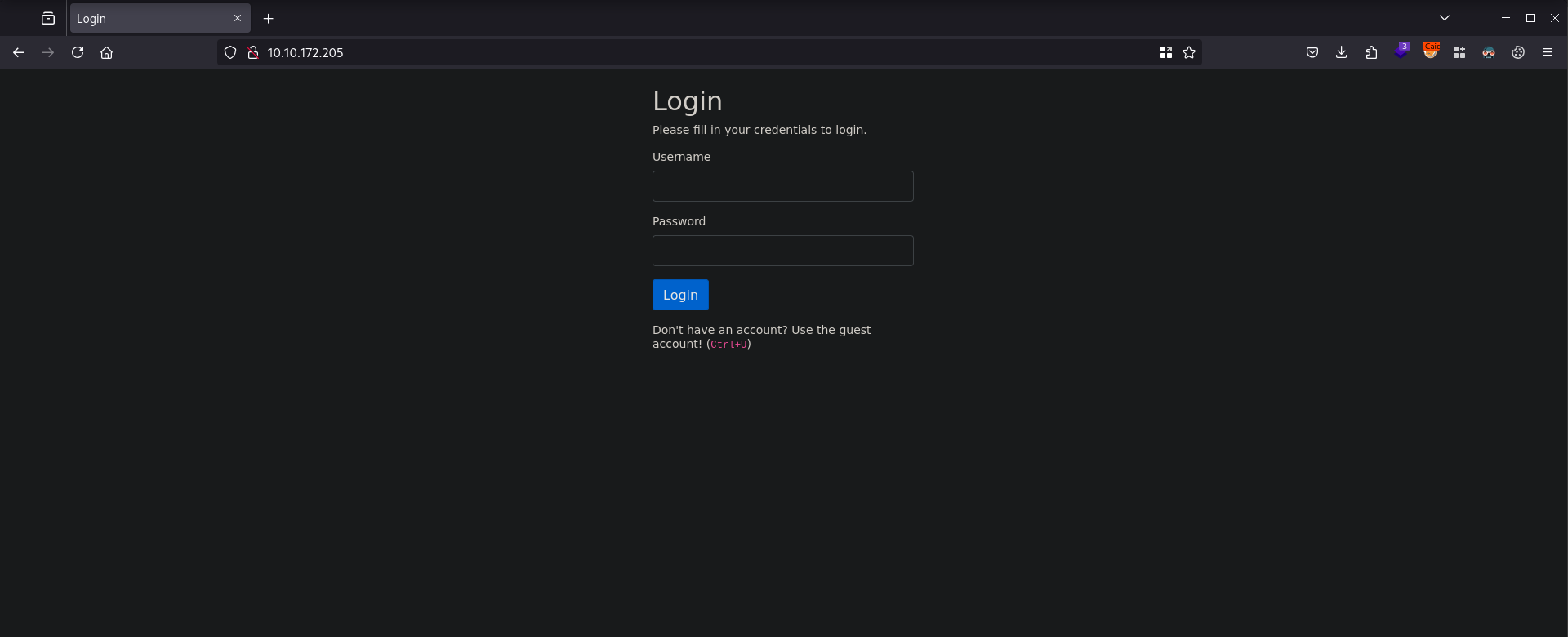
Once the machine has been fully deployed, we are then given a URL to access the web app - http://10.10.172.205. After accessing the URL we are greeted with a login page as shown below.
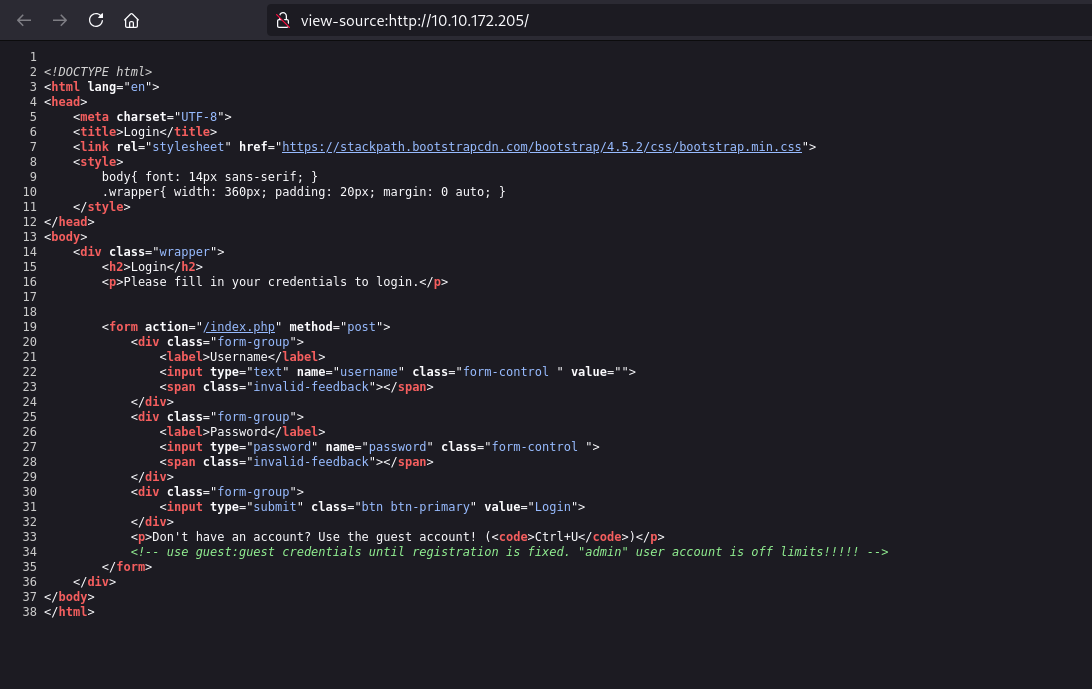
We don’t have much information to access the contents of the website other than the note at the bottom to view the source code of this page. After reviewing the source code, notice there’s a username and password (guest:guest) provided for us to login to the website.
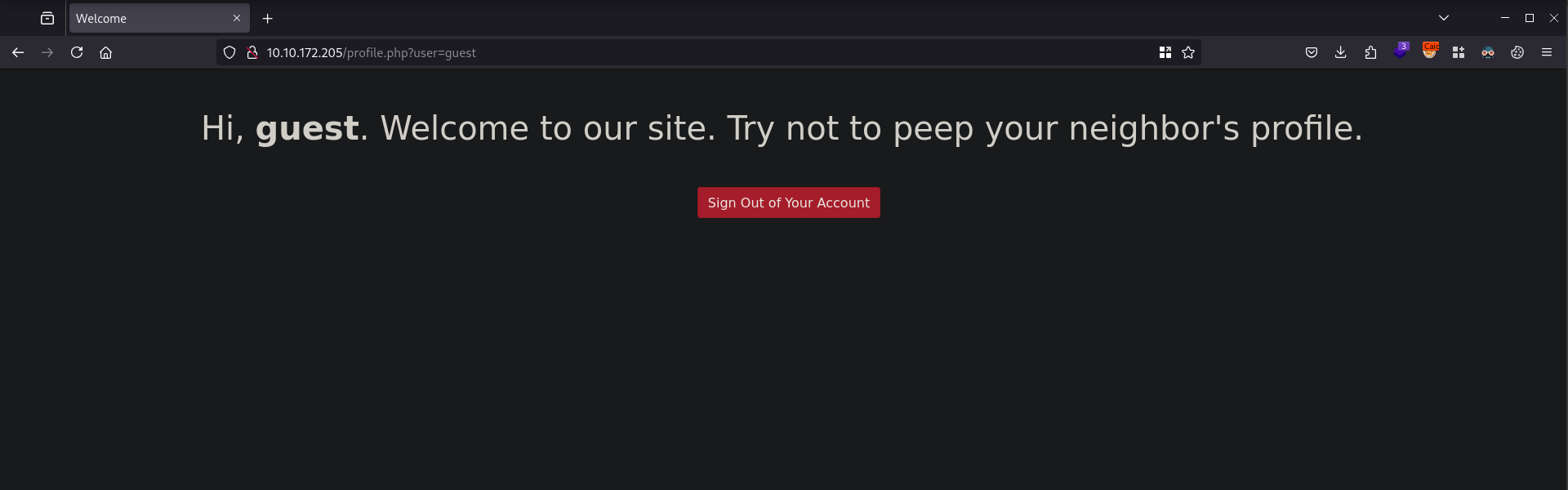
We can then login using the username guest and password guest
Exploiting IDOR
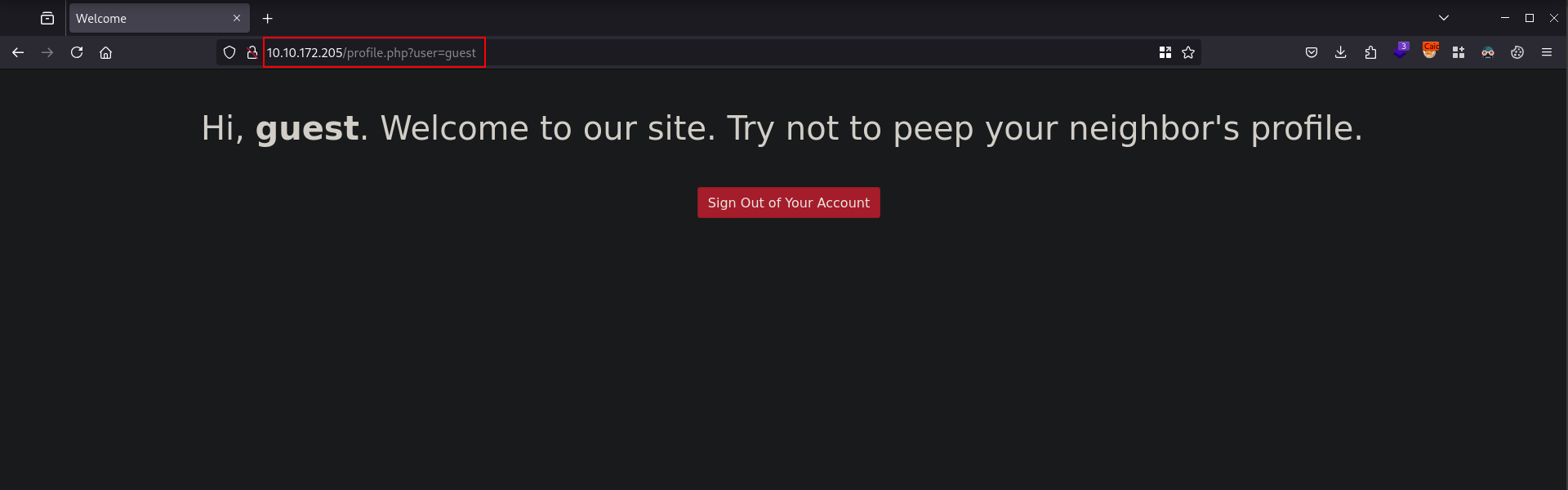
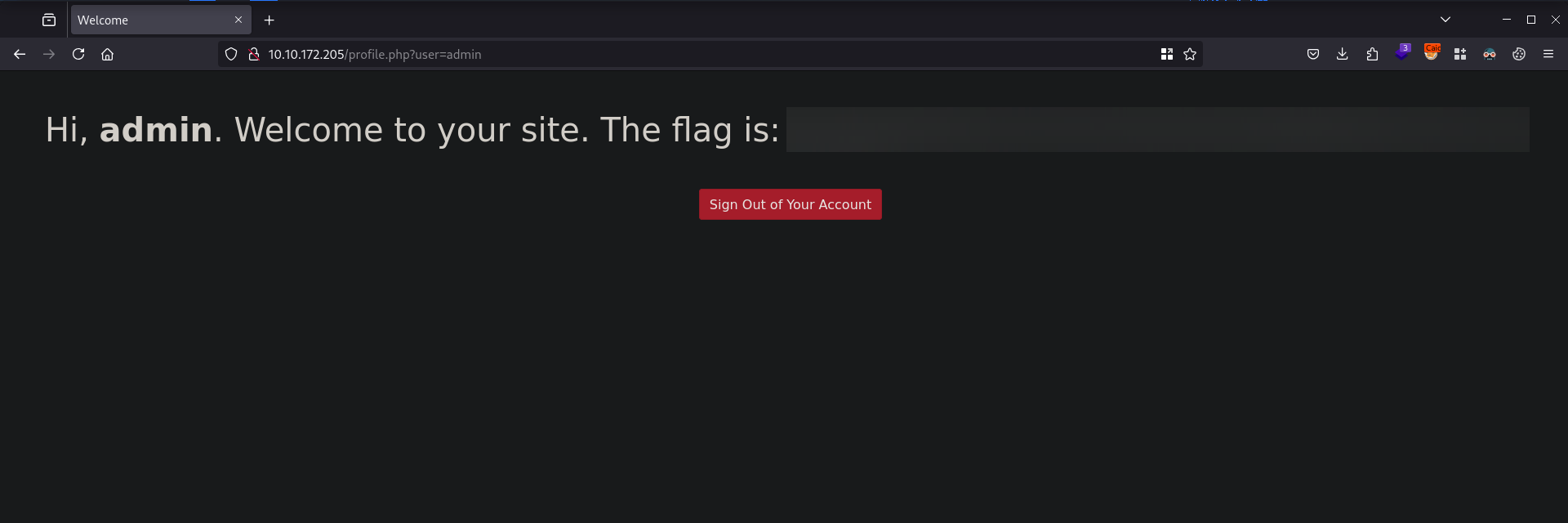
Notice the URL uses a user parameter with a value of the username guest. Since this room is about IDOR, we will then test for IDOR by changing the value of the parameter to another user in hopes of accessing the contents of the other user.
Since we already know that there’s an admin user from the source code, we can try changing the value of the parameter from user=guest to user=admin. After changing, we are now able to access the admin account and the Flag for this challenge.
Thanks for reading my waklthrough, I hope you enjoyed it!